
This chapter describes the router's implementation of the International Standards Organization's (ISO) Open Systems Interconnection (OSI) Connectionless Network Layer. DECnet Phase V supports OSI (hereafter called DECnet V/OSI) and users of DNA V networks can use this chapter for information about the ISO OSI protocols. This chapter contains the following sections:
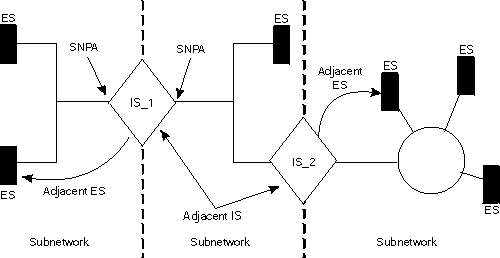
An OSI network consists of interconnected subnetworks. A subnetwork consists of connected hosts referred to as end systems (ESs) and routers referred to as intermediate systems (ISs), as shown in Figure 19.
ESs contain all the layers of the OSI reference model and contain the host applications. ISs perform the functions of the lower three layers of the OSI reference model and handle the routing of the network protocol data units (NPDUs) between subnetworks. ISs logically attach to the subnetwork at the subnetwork point of attachment (SNPA). The SNPA is the access point into the data link layer.
Depending on the IS configuration, each IS can run three protocols: ES-IS, IS-IS, and Connectionless-Mode Network Protocol (CLNP).
The ES-IS protocol enables the ESs and ISs attached to the same subnetwork to dynamically discover each other's existence. An ES connected to the same subnetwork as an IS is adjacent to the IS. The IS-IS routing protocol enables the ISs to do the following:
The CLNP protocol is a datagram protocol that transports packets between ISs.
The NPDU contains OSI network addresses (also called NSAPs). The NSAP refers to a point at the network layer where the user accesses the network layer. NSAPs are unique points within a system that represent addressable endpoints of communication through the network layer. The number of NSAPs may vary from system to system.
An addressing authority, such as the United States government's National Institute of Standards and Technology (NIST), administers NSAP addresses and determines how the addresses are assigned and interpreted within their domain. If desirable, these authorities may further partition the domain into subdomains and designate corresponding authorities to administer them.
There are two NSAP addresses within the NPDU, a destination address and a source address. Each address can vary in length from 2 octets to 20 octets and is usually represented in hexadecimal notation. The following is an example of a 6-octet NSAP that can be entered in the OSI configuration of the router.
AA000400080C
Because the address length is variable, portions of the PDU header called Destination Address Length Indicator and Source Address Length Indicator are used to indicate the length, in octets, of each address.
An NSAP address consists of two parts, an Initial Domain Part (IDP) and a Domain Specific Part (DSP) as shown in Figure 20.
Figure 20. NSAP Address Structure
*-----------*-------------------------------------------------* | IDP | | *-----*-----* DSP | | AFI | IDI | | *-----*-----*-------------------------------------------------*
The IDP consists of two parts, the Authority and Format Identifier (AFI) and the Initial Domain Identifier (IDI).
The AFI specifies the type of IDI and the network addressing authority responsible for allocating the values of the IDI.
The IDI specifies both the network addressing domain from which the values of the DSP are allocated and the network addressing authority responsible for allocating values of the DSP from that domain.
The network addressing authority identified by the IDI determines the DSP. However, what is important is that the DSP includes specific addressing information for the domain.
The IS-IS protocol divides the NSAP address into three portions; area address, system ID, and selector (see Figure 21). The area address and system ID, together with a selector of 0, are referred to as the Network Entity Title (NET). A NET is the address of the network layer itself and is assigned when you configure an IS into the OSI network.
Figure 21. IS-IS NSAP Addressing Interpretation
*------------*----------------------------------------------------* | IDP | DSP | *------------*-------------*-------------------------*------------* | Area Address | System ID | Selector | *--------------------------*-------------------------*------------*
In the IS-IS protocol, the area address is that portion of the NSAP that includes all or a portion of the IDP and the portion of the DSP up to the system ID.
The area address is that portion of the NSAP that identifies a specific area within a domain. This address must be at least 1 octet long and all ESs and ISs in the same area must have the same area address.
The system ID is that portion of the NSAP that identifies a specific system within an area. System IDs must have the following attributes:
The selector is a 1-octet field that acts as a selector for the entity that is to receive the PDU, for example, the transport layer or the IS network layer itself. The router sets this field to 0.
Government Open Systems Interconnection Profile (GOSIP) Version 2 provides for government use the NSAP addressing format illustrated in Figure 22. The authorities responsible for the address have clearly defined the fields and specified the addressing format under the DSP set by the National Institute of Standards and Technology (NIST).
Figure 22. GOSIP Address Format
*-----------*-------------------------------------------------------------* | IDP | DSP | *-----*-----+-----*-------*----------*--------*------*---------*----------* | AFI | IDI | Ver | Auth. | Reserved | Domain | Area | Sys. ID | Selector | | 47 | 0005| 80 | | | (2) | (2) | (6) | (1) | *-----*-----*-----*-------*----------*--------*------*---------*----------*
Multicast addressing is the method that level 1 (L1) and level 2 (L2) ISs use to distribute link-state updates (LSUs) and hello messages to other systems or LANs. When an LSU or a hello message is multicast, a group of destination stations receive the packet. For example, an L1 LSU is multicast only to other L1 ISs. An Intermediate System Hello (ISH) is multicast only to ESs on the same subnetwork.
You can configure multicast addresses for each subnet with the set
subnet command. Table 103 lists the multicast addresses for Ethernet, and
Token-Ring.
Table 103. IS-IS Multicast Addresses
| Destination | Ethernet 802.3 | Token-Ring 802.5 | Address Description |
|
|---|---|---|---|---|
| All ESs | 09002B000004 | C00000004000 | 9000D4000020 | For all end systems on the subnetwork. |
| All ISs | 09002B000005 | C00000008000 | 9000D40000A0 | For all intermediate systems on the subnetwork. |
| All L2 ISs | 0180C2000015 | C00000008000 | 800143000028 | For all L2 intermediate systems on the subnetwork. |
| All L1 ISs | 0180C2000014 | C00000008000 | 8001430000A8 | For all L1 intermediate systems on the subnetwork. |
OSI routes packets using the IS-IS protocol. Routing with the IS-IS protocol is based on:
The IS-IS protocol uses routing tables to forward packets to their correct destinations. The routing table entries are built from information in the link state database or from user-configured reachable addresses. The link state database is built from information received in the link state update (LSU). Refer to the "Link State Databases".
The IS-IS protocol is a link state dynamic routing protocol that detects and learns the best routes to reachable destinations. IS-IS can quickly perceive changes in the topology of a domain, and after a short convergence period, calculate new routes. To accomplish this, the IS uses the following packets:
An IS-IS area is a collection of systems on contiguous subnetworks. Each area's topology is hidden from those of the other areas to reduce routing traffic. A level 1 (L1) IS is used to route within an area. A level 2 (L2) IS is used to route between areas or over the backbone. An IS that routes within an area and over the backbone is considered an L1/L2 IS.
An IS-IS domain is a set of rules, administered by the same authority, that all ESs and ISs must follow to ensure compatibility. There are two types of domains that require discussion, administrative domain and routing domain.
An administrative domain controls the organization of ISs into routing domains as well as the NSAP and subnetwork addresses that those routing domains use.
A routing domain is a set of ISs and ESs governed by the following rules:
When an L1 IS services more than one area, these additional areas are called synonymous areas. A router can support any number of synonymous areas, as long as there is an overlap of at least one area address between adjacent routers. For example, in Figure 24, Area 1 and Area 2 are synonymous areas to each other and Areas 3 and 4 are also synonymous to each other.
L1_A IS in area 2 must have area 1's address added to its configuration and the L1 IS in area 1 must have area 2's address added to its configuration. For areas 3 and 4 to be synonymous, each area's address must be added to the others L1 IS.
The IIH message enables an IS to determine the existence of other ISs and to establish adjacencies. There are three types of IIH messages: L1, L2, and point-to-point.
Each IS contains a local hello timer and holding timer. Each time the hello timer expires, an IIH is multicast over the IS's interface to any adjacent ISs. When the hello message is received, the recipient establishes or updates (refreshes) the adjacency information. This information remains current for amount of time (seconds) specified by the holding timer. If the holding timer expires, the adjacency is brought down.
The L1 IIH message is multicast over the interface when its local hello timer expires. The L1 IS places the following information in its IIH:
Upon receiving this message, the adjacent L1 IS extracts the source ID of the sending IS. This IS then constructs its own IIH message and places its source ID into the source ID field. The sender's source ID is placed into the IS neighbors field. Returning the sender's ID verifies to the sender that the adjacent IS is aware that it exists (2-way adjacency).
When the first IS receives the IIH, it too extracts the source ID and looks at the IS neighbor field. Upon discovering its own source ID in the IS neighbor field, this IS establishes an adjacency with the other IS.
| Note: | Before the adjacent L1 IS can accept the packet, the packet must have a common area address and the same system ID length as the adjacent IS. |
The L2 IIH is multicast over its interfaces for purpose of identifying itself to other L2 ISs. The L2 IS has the same function as an L1 IIH. The L2 IS places the following information in its IIH:
| Note: | Before the adjacent L2 IS can accept the packet, the packet must have the same system ID length as the adjacent IS. |
A point-to-point IIH message is sent out over an IS's non-broadcast interface (Frame Relay or X.25) to identify itself to other ISs. This IS gives the IIH to contain the following information:
A designated IS is selected among all ISs connected to the same LAN to perform additional duties. In particular it generates link state updates on behalf of the LAN, treating the LAN as a pseudonode. A pseudonode is a method of modeling the entire LAN as a node on the network with fewer logical links. Minimizing logical links throughout the domain lessens the computational complexity of the link-state algorithm.
When more than one IS exists on a LAN, each IS compares the following to determine which IS will become the designated IS:
Each L1 and L2 IS contains a link state database. The primary element of the database is the link state update (LSU). The router is responsible for building its own LSU and processing other ISs' LSUs to maintain the database. The L1 database contains information on ESs. Each L1 database is identical for all L1 ISs in the same area. The L2 database contains information on areas and reachable addresses. Each L2 database is identical for all L2 ISs configured in the IS-IS domain. With information from the databases, the Dijkstra routing algorithm calculates the shortest paths to all destinations and builds the routing tables.
To ensure that each L1 and L2 IS maintains an identical database, LSUs are flooded throughout an area or a backbone. Flooding is a mechanism that an L1 or L2 IS uses to propagate an LSU to all L1 or L2 ISs. An L1 IS floods LSUs to L1 ISs only. An L2 IS floods LSUs to L2 ISs only. An L1/L2 IS accepts both L1 and L2 LSUs.
The L1 LSU is flooded to all L1 ISs. The L1 IS gives the LSU the following information:
The L1 pseudonode LSU is flooded to all L1 ISs located in the area. Any L1 IS located on the same LAN that receives the LSU propagates the LSU to all L1 ISs adjacent on all of its other subnetworks. The L1 IS places the following information in its LSU:
The L2 LSU is flooded to all L2 ISs. The L2 IS places the following information in its LSU:
The L2 pseudonode LSU is multicast over the interface and propagated to all L2 ISs located outside the subnetwork. Any L2 non-pseudonode IS located on the same subnetwork that receives the LSU relays the LSU to all L2s located outside the subnetwork. The L2 IS places the following information in its LSU:
An attached L2 IS is a router that knows of other areas. An unattached L2 IS is a router that does not know of any areas other than its own.
When routing, an unattached L2 IS routes packets to the closest attached L2 IS.
An L1-only IS uses one routing table, the level 1 routing table. An L2-only IS contains three routing tables: an L2 area-address routing table, an L2 internal-metric reachable-address-prefix routing table, and an L2 external-metric reachable-address-prefix routing table. An L1/L2 IS contains the L1 routing table and all L2 routing tables. The routing table entries are built from information in the link state database.
The following summarizes L1 routing:
An L2 IS contains three routing tables: an L2 area-address routing table, an internal-metric reachable-address-prefix table (internal), and an external-metric reachable-address-prefix table (external).
The following summarizes L2 routing:
Refer to "Internal and External Routing" for a detailed explanation of the internal and external routing tables.
A routing metric is a value associated with a function of the circuit to indicate the cost of routing over that circuit. For example, the routing metric based on the monetary expense of a circuit would use a low number to indicate a low monetary expense and high number to indicate a high monetary expense of routing a packet over that circuit.
The IS-IS routing protocol uses four routing metrics: default metric, delay metric, expense metric, and an error metric.
The current implementation of the OSI protocol uses the IS-IS default metric only. The default metric, by convention, is intended to measure the circuit's capacity to handle traffic. All ISs in the routing domain must be capable of calculating routes based on the default metric. The other routing metrics are optional. Though they are not used by this implementation of the OSI protocol, they are described below for informational purposes only.
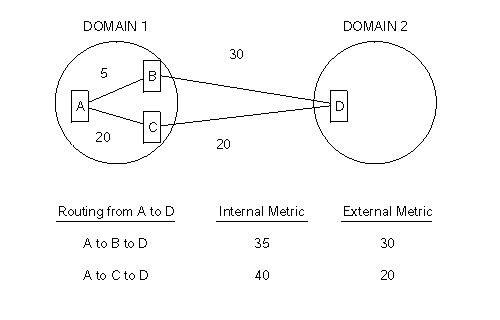
Internal or external routing involves an L2 IS routing a packet between two separate domains. When a packet needs to be routed to another domain, the L2 IS tries to match the address to a reachable address prefix in the internal or external routing table. Internal and external routes are based on the cost (routing metric) to the destination. An internal route's cost considers the cost of routing within the domain and the cost of routing to the destination. An external route's cost is based only on the cost of routing to the destination outside the routing domain. The IS chooses the path with the lowest cost.
For example, a packet is destined to go from node A in domain 1 to node D in domain 2 ( Figure 25). Node A can choose two paths to send the packet, to node B and then on to D or to node C and then on to D. How nodes B and C advertise the cost of their routes to D determines how node A decides to route the packet, internally or externally. There are three possible options:
| Note: | Because there is no exterior routing protocol, all prefix routes between domains must be statically configured. |
Figure 25. Internal and External Routing Metrics
When entering address prefix routes into the router, carefully consider the difference between encoding rules for NSAPs and for prefix routes. The following four examples illustrate address prefix encoding.
For many address prefixes, encoding the prefix and the corresponding NSAP is the same. For example, you are using a GOSIP 1.0 address and you want to create a route to an organization in the DoD. The Org IDI is 1234 and the DoD IDI is 0006. The encoded NSAP address is
4700061234CCCC222222222222
The encoded address prefix is a result of the truncation of the NSAP
4700061234
The encoding rules are about all NSAP formats having a fixed length IDI and to any address prefix ending after the IDP.
An address prefix based entirely on the AFI is encoded only on the 1 octet AFI field. For example, if an address prefix is needed for all X.121 format addresses (used on X.25 networks), you would use the X.121 AFI of 37.
NSAP addresses that have variable length IDI formats, such as X.121, F.69, E.163, and E.164, use a more complicated encoding scheme. When variable length IDIs are encoded as an NSAP, the address is left padded with zeros; however, when the IDI is encoded as an address prefix, there is no left padding.
For example, you want to route X.25 calls from the U.S. to an X.25 carrier in the Netherlands. The carrier has a Data Network Identifier Code (NDIC) of 2041. The encoding of the address prefix would be
372041
An X.25 subscriber having a national telephone number (NTN) of 117010 on this carrier would have an NSAP of
3700002041117010
Notice that the IDI of the NSAP is left padded with zeros to 14 digits because the resulting international data number (2041117010) was less than 14 digits.
If, however, you want an address prefix that points only to this one X.25 subscriber, the encoding would then be the NSAP (3700002041117010), because the prefix does not end in the IDP.
A default address prefix is used when you want to originate a default route to all addresses outside your domain. Default address prefixes are of zero length, so there is nothing to encode.
To provide a minimum layer of security to the network, OSI provides the option of authentication passwords. When authentication is enabled, any IS-IS packet that does not contain the proper password is not accepted by the IS. The authentication field of the NPDU contains the authentication passwords. There are two types of authentication passwords, transmit and receive.
A transmit password is added to IS-IS packets transmitted by the IS. A receive password is a listing of the transmit passwords that the IS accepts. For example, with authentication enabled, if a transmit password is not added to the packet, or a listing of the transmit password is not in the receive password database, the packet is dropped. There are three types of transmit and receive passwords: domain, area, and circuit.
A domain password provides security for L2 routing information. An area password provides security for L1 routing information. A circuit password provides security for IS-IS hello messages.
The ES-IS protocol enables ESs and ISs attached to the same subnetwork to dynamically discover each other's existence and availability. This information also permits ESs to obtain information about each other without an available IS.
Route redirection information enables an IS to inform an ES of a better route when forwarding NPDUs to a particular destination. For example, a better route could be another IS on the same subnetwork as the ES, or the destination ES located on the same subnetwork.
Addressing information is passed on to ESs and ISs through hello messages.
A local configuration timer (CT) and a holding timer (HT) is present on each ES and IS. Each time the CT expires, a hello message is multicast on the LAN. When the hello message is received, the recipient sets its HT value according to the value transmitted in the HT field of the message. The recipient is expected to retain this information until the HT expires to ensure correct operation of the ES-IS protocol.
The ESH message is multicast from the ES to all L1 ISs when its local CT expires. The ES constructs this message to inform an IS of any NSAPs that it serves. Upon receiving this message the IS extracts the NSAP and SNPA information and stores the pair in its L1 routing table, replacing any other information currently stored there.
The ISH message is multicast to all adjacent ESs when its local CT expires. The IS constructs this message to inform the ES of its NET. Upon receiving of this message, the ES extracts the NET and SNPA information and stores the pair in one of its local routing tables, replacing any other information currently stored there.
For X.25 networks, the router establishes X.25 switched virtual circuits (SVCs) on routing circuits.
| Note: | To enable DECnet V/OSI for X.25, you must enter the DECnet IV process and define your router to be a DEC-AREA or DEC-ROUTING-IV router. You must do this (and restart the router!) to enable the commands to do the DECnet V/OSI configuration. Use the define executor type command. |
Routing circuits are point-to-point connections between nodes that implement the ISO CLNS protocol. The router employs these types of routing circuits:
Static incoming and static outgoing circuits have only one SVC associated with them, and they carry both user data and non-user data (such as routing protocol messages). You bring static circuits up and down explicitly using DECnet V/OSI configuration commands. Dynamically assigned routing circuits are established upon data arrival and are cleared when there is no data being transmitted or received. A dynamically assigned circuit can have multiple SVCs, but can carry only user data.
DECnet V/OSI controls calls for each of the types of routing circuits by using filters and templates. Filters are used to process incoming calls; templates are used to establish outgoing calls.
A filter is a collection of user-configurable parameters that define the criteria for accepting all incoming calls for the specified X.25 routing circuit.
The parameters defined in a filter include the calling DTE address, a filter priority, and call/user data.
Incoming calls can be on a static incoming circuit or a dynamically assigned (DA) circuit. One or more filters may be defined for the same routing circuit. For example, a DA circuit can have multiple adjacencies and more than one filter may be defined for that routing circuit.
The list of filters for static incoming circuits and DA circuits are intermixed and ordered by descending priority. When an incoming call is received, the router searches the list of filters, highest priority first. To prevent a static circuit from being erroneously assigned to a DA circuit, it is recommended that the filters of all static circuits be assigned a higher priority than the filters of all DA circuits.
For a static incoming circuit, the filter should specify a particular calling DTE address, but the first octet of the call/user data must contain the ISO 8473 Protocol Discriminator (129). For correct operation of multiple DA circuits, additional constraints should be configured for each defined filter. This ensures that the selection criteria specified in those filters permit the required distinction to be made between incoming calls.
| Note: | If a DA circuit should incorrectly connect to a static circuit, the architecture makes no attempt to identify the condition or rectify the problem. The usual "initialization failure" may be generated on the static side due to non-response to its link initialization queries. The static SVC is then subsequently cleared. |
A template is a collection of user configurable parameters for outgoing calls. It sets the parameters so that the circuit on the remote router accepts the incoming calls. The parameters defined in a template include the calling DTE address and the call/user data.
You can define only one template per outgoing static routing circuit.
Link initialization is a procedure proprietary to Digital Equipment Corporation (and is not part of OSI). Link initialization immediately follows SVC establishment. It is used primarily to establish the DECnet relationship with a remote system on a point-to-point link.
On receipt of an Initialization/XID message, verification can be performed on two levels: on a circuit basis or on a system basis. Basically, the process of verification compares the incoming verification data against data specified locally either for the circuit or for the calling system. The verification data appears in the verification data field of the XID message.
| Note: | This release of the router software does not support verification by the system. |
| Note: | When operating DNA IV networks together with DNA V networks, all DNA IV configuring and monitoring must be done from the DNA IV NCP> configuration process. For information on configuring DNA IV, refer to "Using DNA IV". The use of the term "OSI" in this chapter refers to both the OSI and DNA V environments unless indicated otherwise. |
This section outlines the minimum configuration steps that you are required to perform to get the OSI/DNA V protocol up and running over a LAN (Ethernet or Token-Ring ), X.25 packet switching networks, and Frame Relay. Before beginning any configuration procedure, use the list device command from the config process to list the interface numbers of the different devices. If you desire any further configuration command explanations, refer to the configuration commands described in this chapter.
| Note: | You must restart the router for new configuration changes to take effect. |
Do the following basic configuration procedure before beginning the specialized procedures described in the following sections.
To configure the OSI protocol to run over an Ethernet or over a Token-Ring LAN, set the subnet. There is a one-to-one correspondence between subnetworks and interfaces. Use the set subnet command to configure all LAN subnets (Ethernet, Token-Ring, or . Use the default multicast addresses for Ethernet. When configuring a token-ring, use these addresses:
Use the list subnet detailed or list subnet summary command to verify that you have configured the subnets correctly.
To configure the OSI protocol to run over the X.25 or Frame Relay interface, do the following:
| Note: | The router will prompt you for a DTE address. For frame relay, enter the DLCI (Data Link Control Identifier) number. For X.25 the enter the PSN's DTE address. |
When configuring a DNA V router, you may need to configure an interface to run in a DNA IV environment. For example, the router is attaching to both a DNA V and DNA IV network, or a DNA IV ES is attached to a DNA V router.
Before beginning the steps below, use the appropriate preceding section to configure OSI over a LAN, X.25, or Frame Relay.
DNA IV uses a distance-vector routing algorithm. DNA V can use either a distance-vector or a link-state routing algorithm. The algorithm is selected according to what is enabled and disabled, and combinations that can result from these two protocols: